The cyber-attack on JLR: How a cyber policy would respond
The cyber attack on Jaguar Land Rover (JLR): How a cyber policy would respond
In August 2025, Jaguar Land Rover (JLR) suffered a major cyberattack that forced the shutdown of its global IT systems and production facilities, including key operations in the UK, Slovakia, China, and India.
The attack, claimed by the hacker group “Scattered Spider” and the same group which claimed the attack on M&S earlier in the year, halted vehicle assembly, disrupted retail operations, and delayed new car registrations during a peak sales period.
While JLR initially reported no customer data theft, it later confirmed that some internal data had been compromised, and regulators were notified. The incident highlights the operational fragility of modern manufacturing, where a single breach can paralyze production lines and supply chains within hours.
How would a cyber policy respond?
An industry standard cyber insurance policy would have responded swiftly to the JLR incident by covering a range of critical exposures. First, it would cover the costs of forensic investigation, crisis communications, system restoration, and legal counsel to manage regulatory notifications and compliance. Second, it would provide financial support for business interruption losses due to halted production. If data was compromised, the policy could also extend to liability protection, including defence and regulatory expenses.
Importantly, cyber policies include access to specialist incident response teams, where required, helping manufacturers contain threats quickly and resume operations as soon as possible. If a ransom is demanded, then the policy will respond by providing access to specialist ransomware negotiators and cover the costs of paying the ransom. The below graphic maps out the costs likely associated with the JLR attack and the coverage which would be available on an industry standard cyber policy.
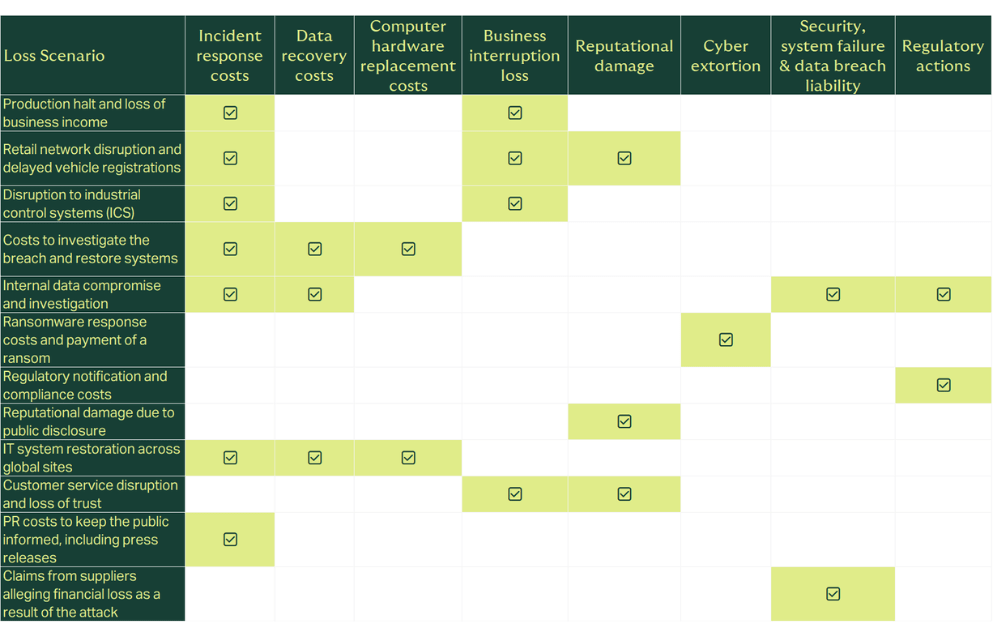
Does my policy cover my organisation’s loss of income if we cannot operate because of a cyberattack which impacts one of our suppliers?
Business interruption costs are included in cyber policies as standard, including where the disruption is caused by a third-party IT supplier. Sometimes coverage for supplier outages extends to non-IT suppliers, such as suppliers of component parts, with whom the customer has a written contract. This coverage recognises and aligns with the reliance on supply chains in the manufacturing sector.
Am I covered if the threat actors not only shutdown our production facilities but also cause our machinery to breakdown or become damaged?
This coverage is widely available to organisations in the manufacturing sector. Policyholders have the option to purchase a policy which covers both the physical damage caused by a cyber event as well as the costs associated with responding to the event as outlined above. It is often the case that manufacturers are reliant upon operational technology (OT) to operate their production facilities, which is connected to the physical machinery. Rates are often very competitive for physical damage coverage, and policies can be drafted in a way which fills in gaps in traditional Property Damage and Business Interruption policies, often because of a cyber exclusion.
How quickly can we get support if we were attacked?
Support is available within minutes. Most cyber policies include access to a 24/7 incident response team, breach coaches, forensic investigators, and legal advisors. In a typical scenario, once an attack is reported, insurers activate their panel of experts to contain the breach, assess damage, and begin recovery. Insurers also support the use of your own vendors to respond to a cyber event. For example, some organisations have a trusted relationship with a law firm which specialises in cybersecurity and can support in deploying forensic investigators and ransomware negotiators where required, as well as draft letters to regulators in the event of a data breach. It is important to check with your insurance broker that any firms you engage the services of in the event of a cyber incident is pre-approved on your cyber policy.
Can cyber insurance help us meet regulatory obligations if data is compromised?
Yes, cyber insurance covers costs associated with regulatory compliance following a breach. This includes legal costs associated with navigating GDPR and other data protection laws, notification to affected individuals and the ICO or other regulatory bodies, credit monitoring costs for the individuals impacted, fines and penalties where insurable by law and support from PR firms to manage the reputational impact of a data breach. Cyber insurance also covers the costs, and any subsequent damages, in responding to claims against the policyholder from third parties seeking compensation because of the data breach or failure of security.
What are insurers looking for when underwriting cyber risk in manufacturing?
We survey the cyber insurance market on an annual basis to determine the impact of different risk factors on their underwriting appetite for different industries. Some of these include the strength of the insured’s cybersecurity posture, the reliance on technology to generate revenue and the number of data records held.
For manufacturing firms we encourage that you are able to showcase your ability to recover from cyber attacks and protect your daily income, including incident response and business resilience plans, robust technical controls such as MFA and EDR, supply chain risk management, and your ability to protect your production facilities from attacks against your operational technology. For property damage coverage, insurers will need to review your statement of values in relation to your physical property.
Can you help us to determine how much cyber insurance we should be purchasing, and how much it will cost us?
Yes, we can provide peer benchmarking in respect of limit, retention and premium. We can also provide cyber loss modelling to help you determine the total costs associated with different types of cyber events. Further, we can benchmark your cybersecurity controls against your peers to help support areas of improvement and our market tracker tool provides insights into the most appropriate insurance providers for your risk profile. Our cyber risk specialists can help you to unbox all this information and align it with your risk appetite, to determine the best strategy for your organisation from a risk control standpoint.
What do we do next?
The cyber-attack on Jaguar Land Rover serves as a stark reminder of the operational and financial vulnerabilities facing modern manufacturers. As production facilities become increasingly digitised and reliant on interconnected systems, the risk of disruption from cyber threats grows exponentially. A well-structured cyber insurance policy not only provides financial protection but also delivers rapid access to expert support, helping organisations recover swiftly and meet regulatory obligations. Reach out to your Howden representative to discuss the different ways in which we can support your cyber journey.
Disclaimer: This is an overview guide only, and policy terms will vary. You should review the specific terms of your own coverage in the event of an incident. If you have any queries please contact your Howden broker.
If you’d like to discuss or explore insurance solutions to safeguard against emerging threats, please reach out to Daniel Lewsley.
