What to do when you're a victim of a Cyber-attack
Published
Read time
Being a victim of a cyber-attack can be devastating for a business, but what do you do when it happens?
We walk you through what you should do when a cyber-incident takes place and explain the insurance process from how a matter is first notified, up to indemnity being confirmed by the insurer.
It can be a complicated process, and there are pitfalls to avoid, which those who are not familiar with how a cyber-policy responds may not know about.
By the end of this guide, we hope you will feel more comfortable with what to do if you’re attacked, and with the cover available under most cyber insurance policies.
Day 1: “The Incident”
Steven is a director of AN Other Company (“ANOC”). At 8am on Monday morning, he arrives at the office and turns on his desktop computer. His computer displays the following message:
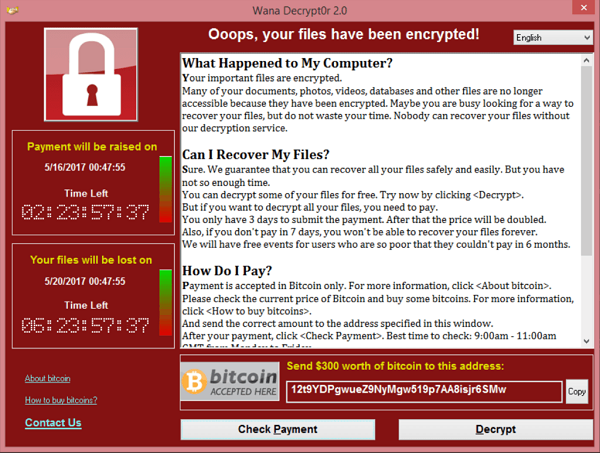
Steven’s colleagues find their computers all show the same message as his. All of the firm’s computers and servers have been locked as part of a ransomware attack. What would you do if you saw this message?
Howden Comment:
The above screenshot is actually taken from “Wannacry” attack, which started in May 2017, and attacked over 200,000 computers across 150 countries. As of June 2017, a total of 327 payments had been made to the attackers, totalling $130,634.77. Although never proven, it is widely believed that this was a state sponsored attack.
“The Notification”
After some initial panic, Steven’s IT Manager reminds him that the firm has cyber insurance with ABC Insurance, so they ring the Account Executive at their insurance broker, DEF Brokers. The account executive provides Steven with the telephone number of a 24 hour Cyber incident emergency helpline run by insurers, and says that a member of the DEF claims team will also be in touch with him shortly.
Howden Comment:
Your broker will make a notification to insurers on your behalf, however as most Cyber incidents are happening “live” it’s often better for the policyholder to call the helpline direct, as the handler at the insurance company will want to know exactly what is happening, and direct contact prevents potential delay and miscommunication. A follow up notification to your broker should then be made.
Steven rings the number, which is answered by Sarah from GHI Loss Adjusters (law firms can also fulfil this role, who are known collectively as “Breach Coaches”) as GHI have been appointed the Cyber incident first responders on behalf of ABC Insurance. Steven and Sarah have a long conversation about what has happened, which leads to Sarah telling Steven that she is going to appoint CyberExpert (a forensic IT specialist company) to urgently have a call with Steven to discuss the next steps with him. Sarah also informs Steven that any appointment is without prejudice to policy cover, so instructions will be required from ABC Insurance before cover can be confirmed.
Howden Comment:
This sort of outsourcing agreement with GHI is quite common in the cyber insurance market. Use of the insurer helpline is generally a requirement of cover, and using insurer-appointed experts avoids the need to obtain insurer consent (and so saves time). However this can cause issues in fast moving incidents, particularly when cover hasn’t yet been confirmed and expert and legal fees are quickly starting to mount up.
“The Cyber Insurance Policy”
Concerned by Sarah’s comment that cover for his claim is not yet confirmed, Steven speaks to Gareth from the DEF claims team. Gareth requires some basic information from Steven, and wants to talk him through some of the details of his Cyber insurance policy. Gareth tells Steven that his policy should provide the following relevant cover (inter alia), as long as there has been a “Cyber Event” as defined by the policy:
- Cover for legal representation with regard to notifying regulators, drafting privacy notices and notifying affected individuals, defending third-party claims, and defending regulatory investigations arising from the Cyber Event.
- Cover for costs to engage an expert to identify the source of the Cyber Event, conduct a forensic examination of the systems and remove any identified malware or other malicious software.
- Reimbursement of any ransom paid as a direct result of any ransomware or other malware introduced to the computer systems as a result of the Cyber Event, providing that this is insurable at law, and not for example, to a country or an individual under sanctions.
- Business interruption cover for lost revenue, and/or the increased cost of working. This provides cover for the three months after the incident, but excludes the first nine hours, which is known as the policy waiting period.
Howden Comment:
Examining the definition of a “Cyber Event” (or similar) in the policy is the key to understanding the extent of cover available. The specifics of this depend upon the wording, with policies varying in whether they extend to, for example, breaches of outsourced IT provider systems. We would expect the majority of policies to respond to data breaches, unauthorised access to systems and ransomware attacks. It’s common for Cyber policies to have over six insuring clauses, and cyber incidents can trigger cover under multiple insuring sections. If this sort of incident happens to you, Howden has a number of specialist Cyber claims handlers who will be able to talk you through the extent of cover available under your policy.
Gareth tells Steven that his policy has a £5,000 excess.
Howden Comment:
Many policyholders aren’t aware that nearly all Cyber policies are inclusive of all relevant costs and expenses. This means that the policyholder here will pay the first £5,000, whatever that applies to – whether a claim settlement, or fees incurred by a forensic expert or legal advisor. In addition to this, the policyholder will be expected to pay any VAT, if they are registered and able to later reclaim it from HMRC. However, even if multiple insuring clauses are triggered, only one excess is ever payable. A forensic expert can very quickly incur costs in excess of £10,000, so if the policy has a low excess, it’s important that confirmation of cover is obtained from the insurer as soon as possible.
“The Meeting”
An online meeting is held to discuss the next steps. Steven, Gareth, Sarah and a number of representatives of ANOC’s IT department attend the call, along with a representative from CyberExpert, who is based in the US. An early decision is taken not to pay the ransom, so the majority of the discussion relates to the rebuilding of ANOC’s network and systems as it is established that they do not have any viable backups. At this very early stage, it is not known whether any data has been exfiltrated. Sarah indicates that she will be appointing a legal advisor to assist ANOC with any data breach issues, including consideration as to whether a notification is required to the Information Commissioner’s Office (“the ICO”).
After the initial meeting, Gareth is able to speak to Jane at ABC insurance. Jane is the allocated in-house claims adjuster who Sarah reports in to. They discuss the incident, and Sarah is able to confirm to Gareth that the ransomware attack falls within the definition of a “Cyber Event” as defined by the policy, meaning that CyberExpert’s costs and also any legal data breach costs will be covered by the policy, subject to the initial £5,000 excess.
Howden comment:
Some insurers (but not all) have Service Level Agreements (“SLAs”), which set out how quickly they need to respond to certain events after an incident, including providing a response on policy cover. In a serious, large scale incident where data has potentially been exfiltrated from the policyholder’s systems and needs to be reviewed, forensic and legal costs can be in excess of £350,000. Where the total policy limit of indemnity is under £1M, this can be exhausted quickly, once third party and business interruption claims are taken into account. If you think you could be in this situation, speak to your broker as soon as possible, who will be looking to explore if there is cover available to you under any other policies, such as Professional Indemnity, which can sometimes provide cover for third party claims.
“Next Steps”
With CyberExpert’s help, ANOC’s IT department is able to restore some basic system functionality, and back ups are implemented. New laptops are purchased, and ANOC is able to recommence trading, albeit at a significantly reduced level. Work begins on setting up a new network to fully restore functionality, and over the course of the next few weeks services are transitioned over to this new network.
A precautionary notification is made to the ICO, and investigations eventually conclude that no data was exfiltrated during the attack, so as a result, the ICO takes no further action.
Along with the costs of the third-party vendors, ANOC’S cyber insurance policy pays for the IT staff overtime incurred in dealing with the incident, and a Forensic Accountant makes a determination on a lump sum payment for the trading losses suffered and additional costs incurred whilst the system was offline.
Howden’s recommendations
Almost all organisations now rely on effective IT networks for business operations. An incident such as the above is one of the worst issues that can happen to a business, particularly if it involves an e-trading operation. A cyber policy cannot prevent this, but it can mitigate the seriousness of the incident, and provide a level of technical and financial support for the affected organisation that may make the difference between them being able to continue, or having to cease trading.
These are our key recommendations to reducing the general risks and likely causes of these incidents:
- Know the details of your policy and keep a hard copy accessible (but secure) in case of a systems outage, complete with relevant contact and notification details.
- Have a BCP (Business Continuity Plan) that sets out how your organisation would deal with a cyber-attack. Ensure that this covers and delegate out the key tasks, such as who will deal with insurers, who will liaise with IT services, and who will be responsible for purchasing new hardware.
- Review how regularly back-ups are kept up to date, and ensure that if required, the process for requesting and implementing them is simple and just as importantly, quick.
- Keep a record of the firm’s basic hardware requirements such as laptops and servers that might need to be replaced at short notice after a ransomware attack.
- Ensure that any critical software updates are installed immediately upon release.
- Keep passwords safe and train staff to spot phishing emails.
- Apply two factor authentication to all live user accounts and ensure dormant accounts are closed as quickly as possible to prevent exploitation
For more information on the topics discussed in the article please contact Ian Barrett.
Ian Barrett - Senior Claims Executive